文章索引
ovpn over mikrotik
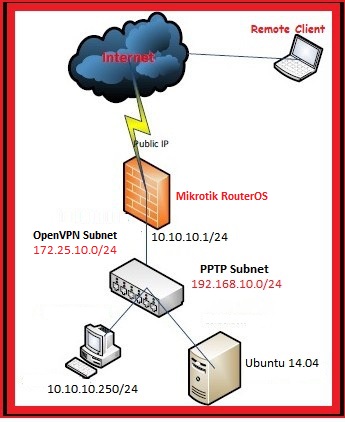
In this post, I’ll describe the step by step procedure to setup Mikrotik RouterOS as OpenVPN server. I’ll use the Ubuntu Server in order to create CA, server and client(s) certificates.
In this post, I’ll describe the step by step procedure to setup Mikrotik RouterOS as OpenVPN server. I’ll use the Ubuntu Server in order to create CA, server and client(s) certificates.
Please remember a few things about Mikrotik OpenVPN server implementation:
- UDP mode is not supported, only supports TCP mode
- username/password is must even though client certificates are being used for authentication
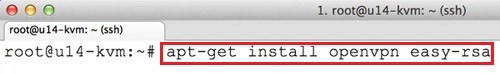
Install the openvpn package on Ubuntu Server using the following command:
Page No
sudo apt-get install openvpn easy-rsa
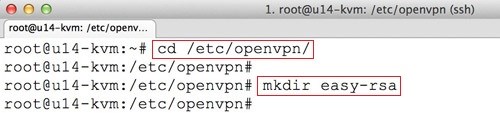
Make an easy-rsa directory inside /etc/openvpn:
cd /etc/openvpn/ sudo mkdir easy-rsa
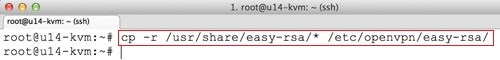
Use the following command to copy the default easy-rsa into /etc/openvpn/easy-rsa for setting up Certificate Authority (CA), certificates and keys generation for OpenVPN server and clients:
cp -r /usr/share/easy-rsa/* /etc/openvpn/easy-rsa/
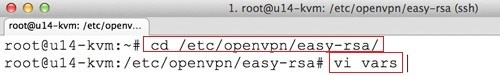
Edit /etc/openvpn/easy-rsa/vars:
cd /etc/openvpn/easy-rsa/ vi vars
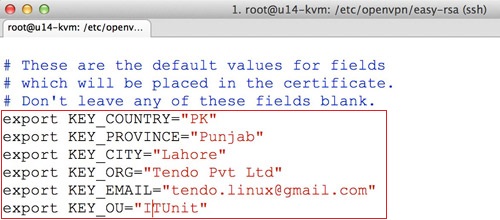
Edit these parameters according to your need:
export KEY_COUNTRY="US" export KEY_PROVINCE="NC" export KEY_CITY="Winston-Salem" export KEY_ORG="Example Company" export KEY_EMAIL="
该E-mail地址已受到防止垃圾邮件机器人的保护,您必须启用浏览器的Java Script才能看到。
"
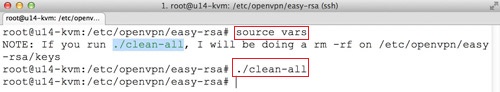
Run the clean-all command:
source vars ./clean-all
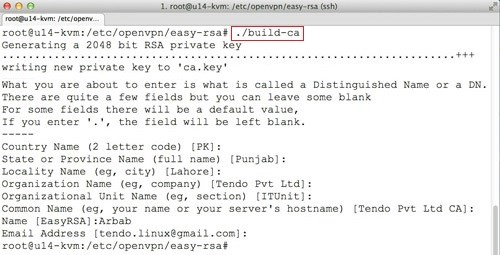
Now, generate the CA certificate:
Page No
./build-ca
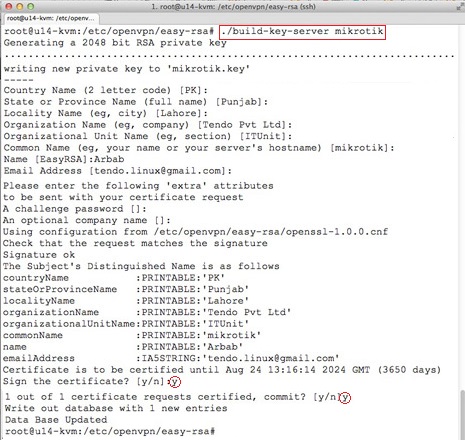
Next, generate a server certificate and private key:
./build-key-server mikrotik
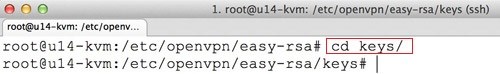
Move to the keys directory (/etc/openvpn/easy-rsa/keys):
cd /etc/openvpn/easy-rsa/keys/
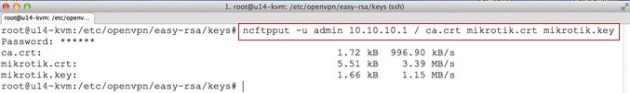
Copy the ca certificate, server certificate and key to the mikrotik router:
ncftpput -u admin 10.10.10.1 / ca.crt mikrotik.crt mikrotik.key
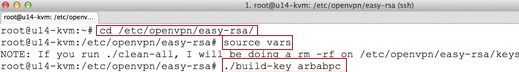
VPN client also need a certificate to authenticate itself to the server. Move to the /etc/openvpn/easy-rsa/directory and create the different certificate for each client:
cd /etc/openvpn/easy-rsa/ source vars ./build-key arbabpc
Mikrotik OpenVPN Server Configuration:
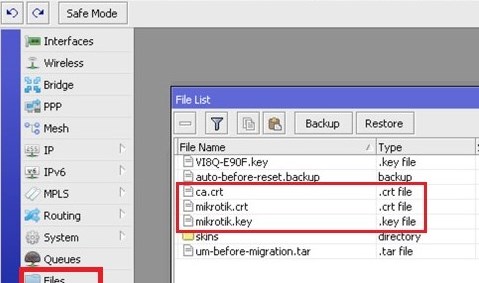
1) Connect to the Mikrotik using Winbox. Goto the Files,there you will find all the files, that you have copied from Linux server:
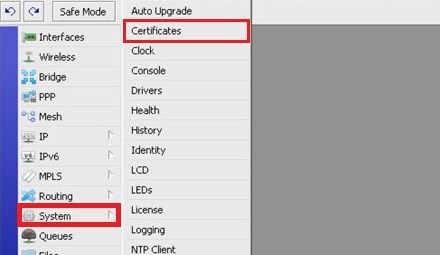
2) Then goto the System —> Certificates:
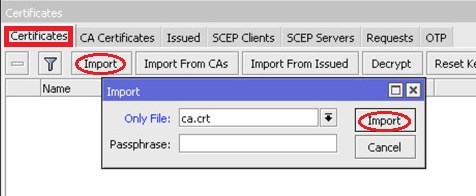
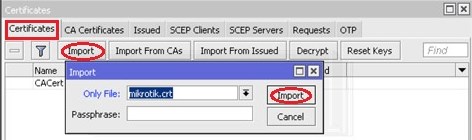
Click on Import Button, then select the ca certificate file (in my case, it is ca.crt) and press Import:
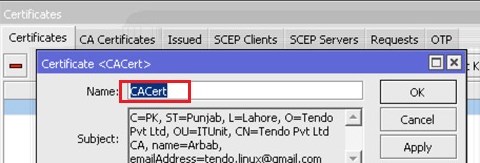
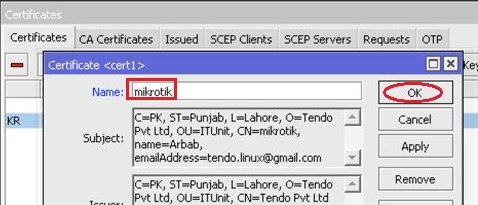
Double click on the imported certificate and change its name (This step is optional):
Once again,click on Import Button, then select the server certificate file (in my case, it is mikrotik.crt) and pressImport:
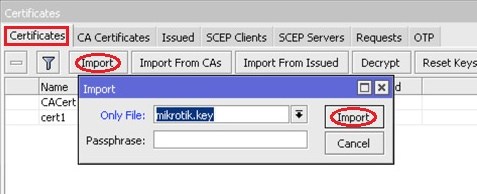
Next, import the server key using the above step:
Double click on the imported server certificate and change its name (This step is optional):
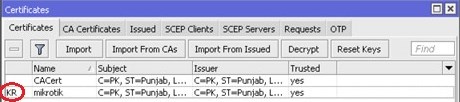
Once you have imported the private key, the server certificate will get the “KR” written in-front of it:
K: Decrypted-Private-Key R: RSA
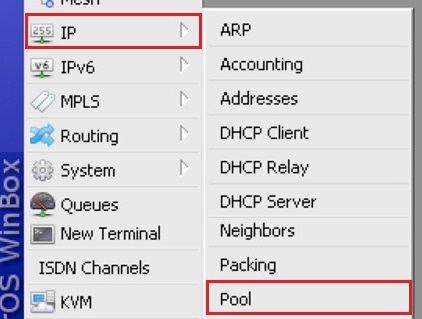
Next we need to create the pool for openvpn client, for this, goto the IP—->Pool:
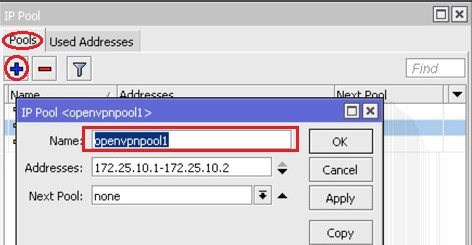
Create each pool of /30 subnet:
Page No
(Reason to create the /30 subnet is that, I am getting the below mentioned error on Windows machine, and that trick work for me)
There is a problem in your selection of --ifconfig endpoints [local=172.25.10.2, remote=172.25.10.1]. The local and remote VPN endpoints must exist within the same 255.255.255.252 subnet. This is a limitation of --dev tun when used with the TAP-WIN32 driver. Try 'openvpn --show-valid-subnets' option for more info.
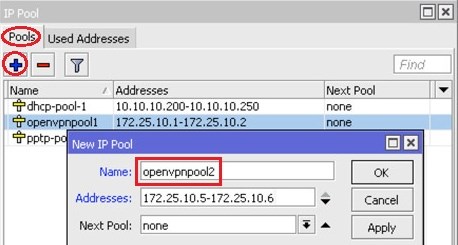
Create as many pool as you have openvpn clients:
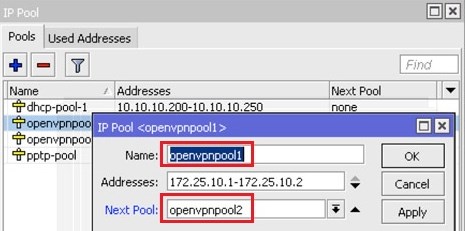
Give in the name of the immediately next pool name in the “Next Pool” field:
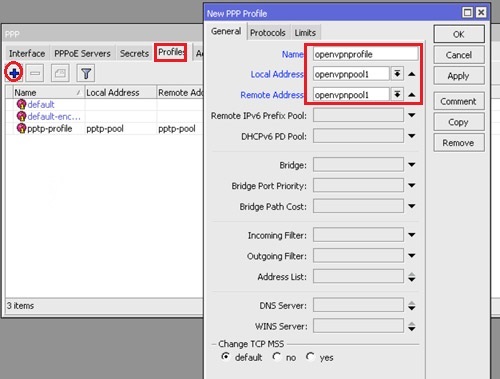
Create the profile for openvpn client by selecting “Profiles” tab and click on + button:
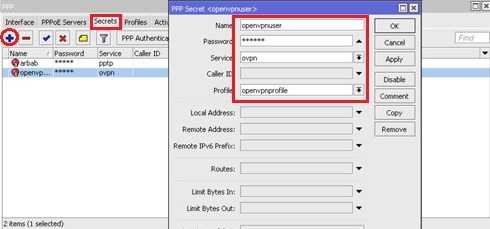
Move over to the Secrets tab and click on the + button to create user for openvpn client:
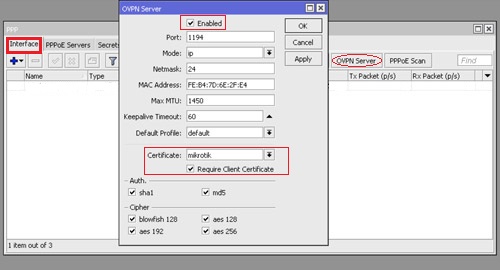
Enable OpenVPN Service and Select Valid Certificate by moving to the Interface take and click on “OVPN Server“:
Windows as OpenVPN Client installation & Configuration:
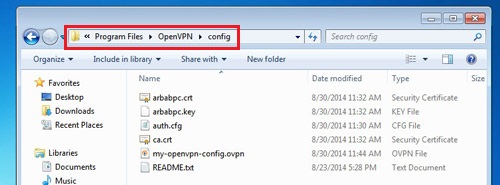
Download free OpenVPN client for windows from here, and install it. Once it’s installed, move to the openvpn directory(C:\Program Files\OpenVPN\config):
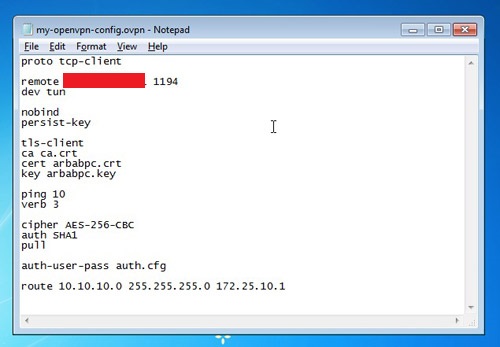
Download the sample configuration file from here. Modify it as per your requirement:
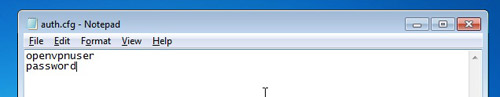
Create the auth.cfg file inside the C:\Program Files\OpenVPN\config folder, with the openvpn username and password that you have created on mikrotik server:
Run the OpenVPN client with Administrator privileges:
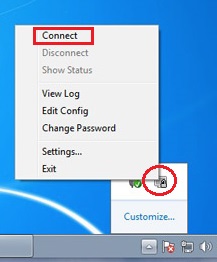
Right click on the openvpn icon at System Tray and click on “Connect“:
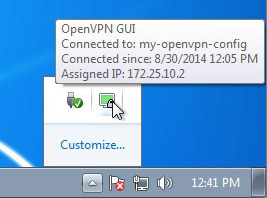
Once, it will be connected, will show you the similar detail:
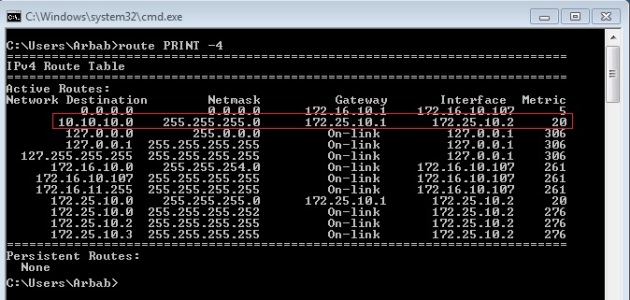
Check the Routing Table:
route PTINT -4
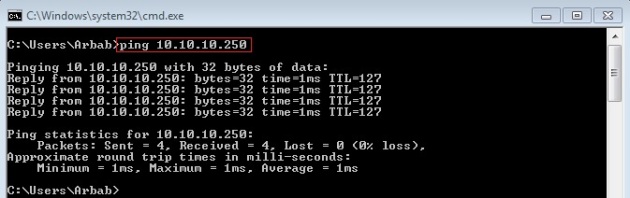
Ping to the internal host:
Success
Hope this will help you!
Please Remember me in your prayers!